How to enable Multi-Factor Authentication (MFA) for S3 buckets?
With AWS CLI commands and Google Authentication App
The security of any company should be a key priority with so many different services accessible in the cloud. The preservation of data should indeed be at the core of every business avoiding unintended deletion. By configuring buckets to delete with MFA, you could offer a degree of additional protection to the AWS S3, which can assist prevent accidental bucket deletion and its contents.
Now in this blog, I will try to put comprehensible steps of How to enable Multi-Factor Authentication (MFA) for S3 buckets? and at the same to time how to delete the MFA
So here are the prerequisites for MFA
- AWS account with root user access ( To activate MFA )
- AWS CLI installed on your local system
- MFA Device ( Oauth App or any MFA apps )
Now MFA in Amazon S3 can only be configured with AWS CLI and there is no other way around this. So let's get started...
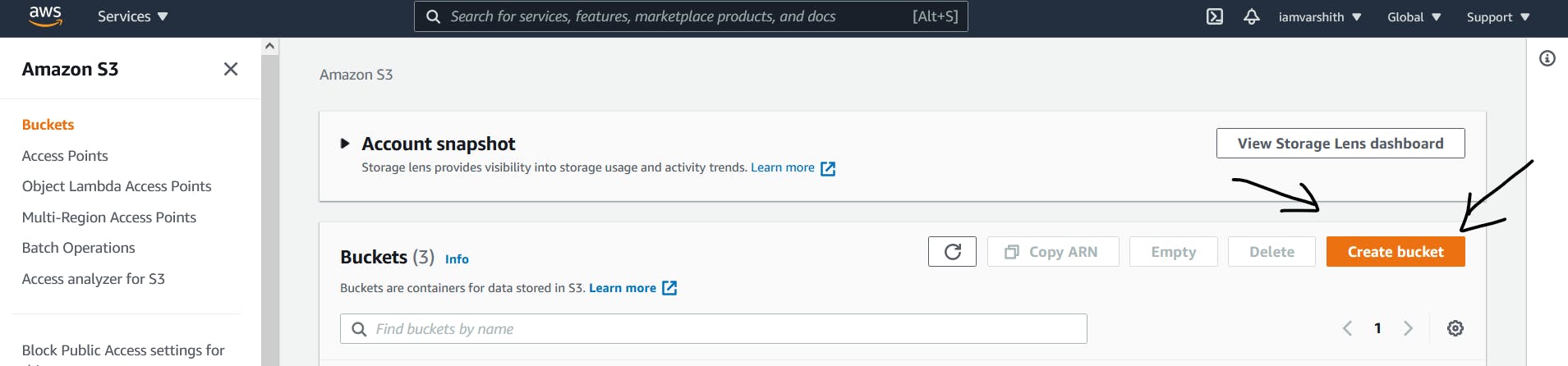
- First and very foremost let's head on to AWS and create an S3 bucket but remember MFA can only be activated for Versioned buckets. And also the bucket's name should be unique, So I have chosen mfatestbucket as the bucket name.
Now once you click on Create Bucket button you will be redirected to a new page just like displayed below
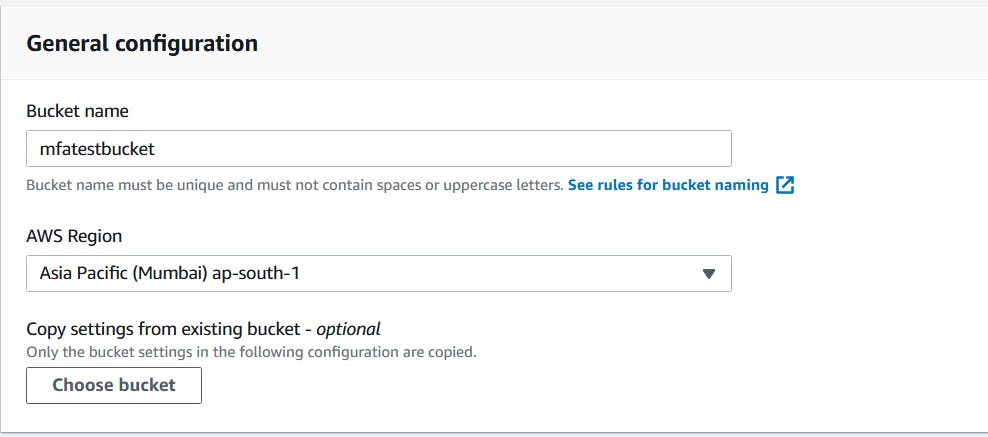
On this new page, you are required to give a name for your bucket. Remember that bucket's name should be unique. And chose your region. Since I am in India and ap-south-1 is the closest data center for me I have chosen this. But you are welcome to pick any of the AWS regions you want. And can also copy setting from existing buckets if you wish to.
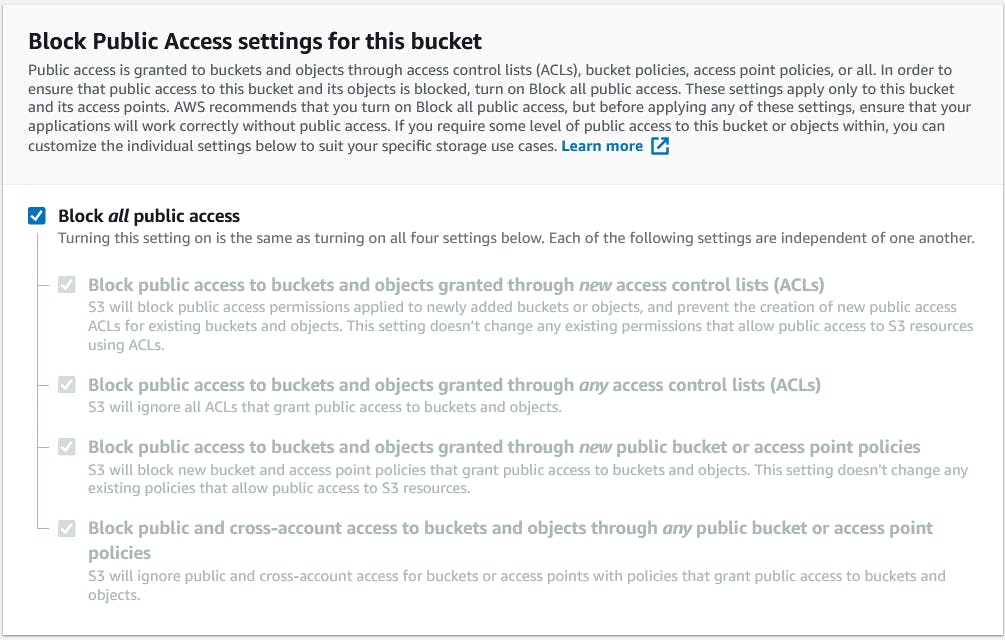
Block Public Access setting - Remember it is always efficient to let your buckets be Private and available from the public. But sometimes S3 can be used to deploy static websites. In such cases, you are required to let your bucket be public.
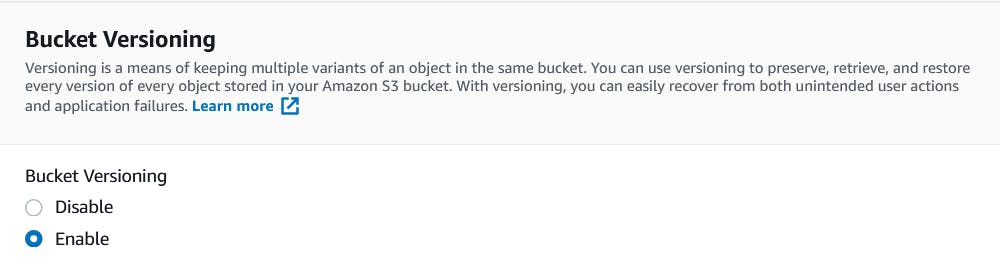
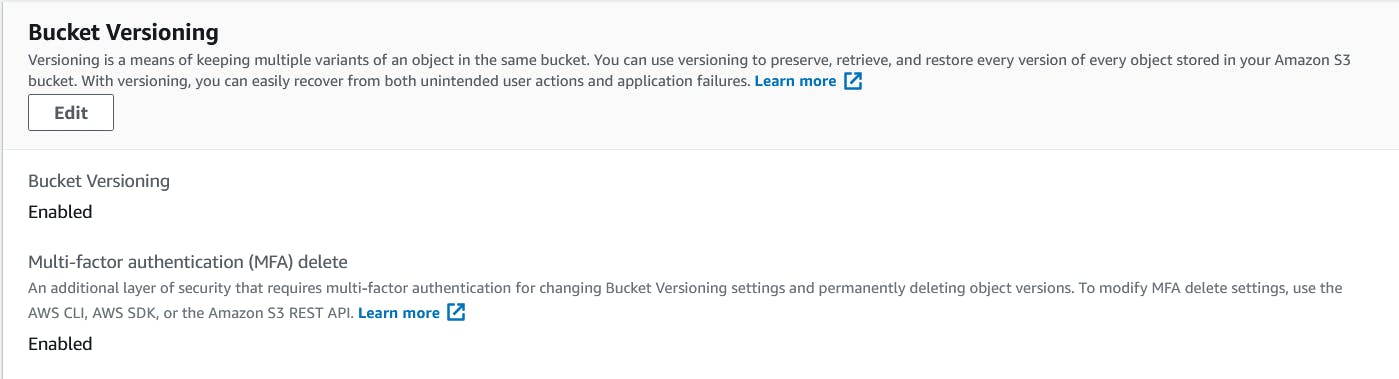
Bucket Versioning - Amazon S3 versioning is a way of maintaining several item versions in the same bucket. The S3 versioning capabilities allow you to save, recover and restore each version of any item stored in your buckets. By versioning, both unexpected user activities and program faults may make it easier to recover. If Amazon S3 receives several requests for writing the same subject at a time, it saves all those objects once versioning is enabled for a bucket. And It is also required to Enable MFA in S3 Buckets
Additional options- There are some additional options like Tags, Encryptions, etc. But in this block, I am interested in concentrating only on enabling MFA from AWS CLI. But feel free to explore.
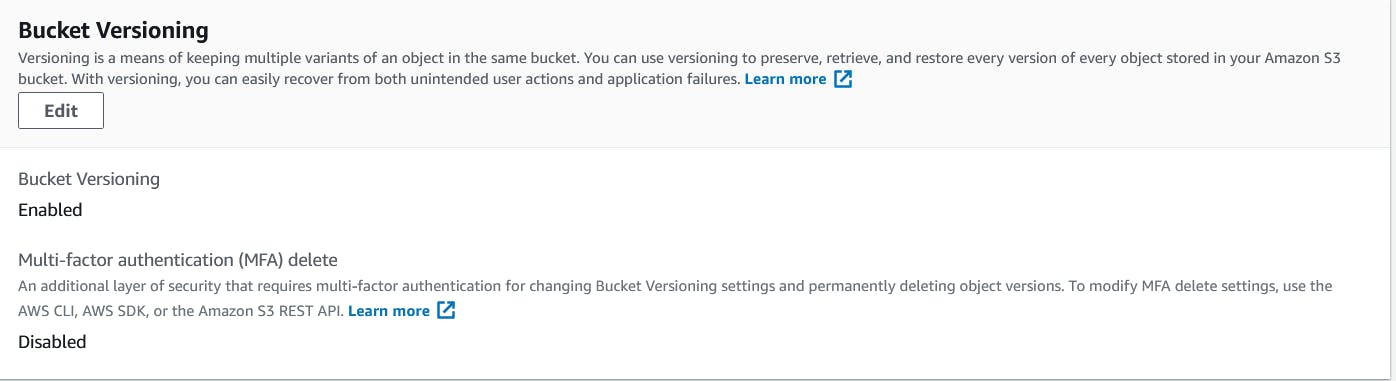
Now the bucket has been created with versioning we can check this by going to mfatestbucket properties. Here we can see that the properties and in these properties, we have Bucket Versioning. Which says the Bucket Versioning is enabled but the MFA is Disabled
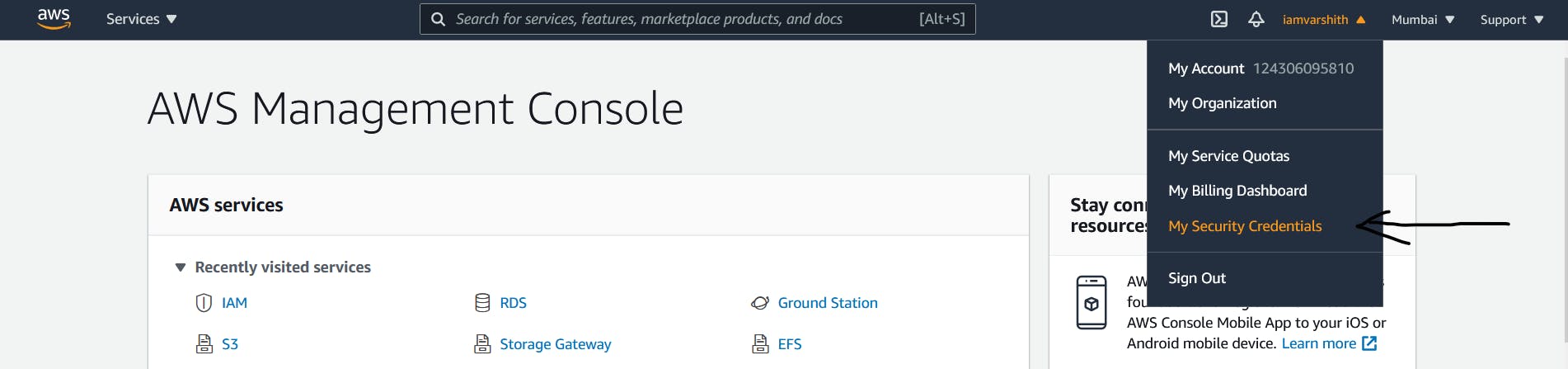
And it is time to go to MFA enabling process. By going to the security credentials page as shown below.
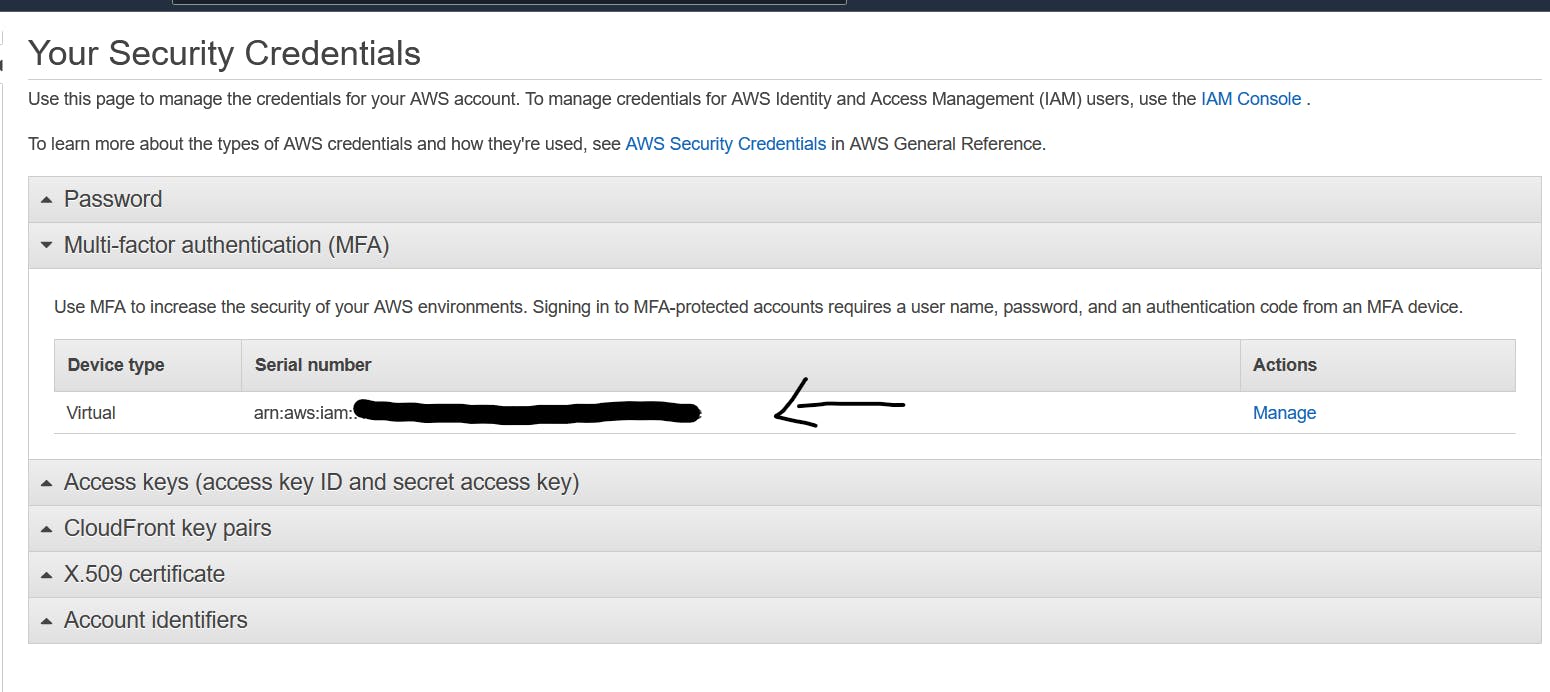
And then you will reach Your Security Credentials page which is used to manage the credentials for your AWS account. In there you can see the MFA option just like displayed below and click on that to add the MFA with your Google Authentication app...
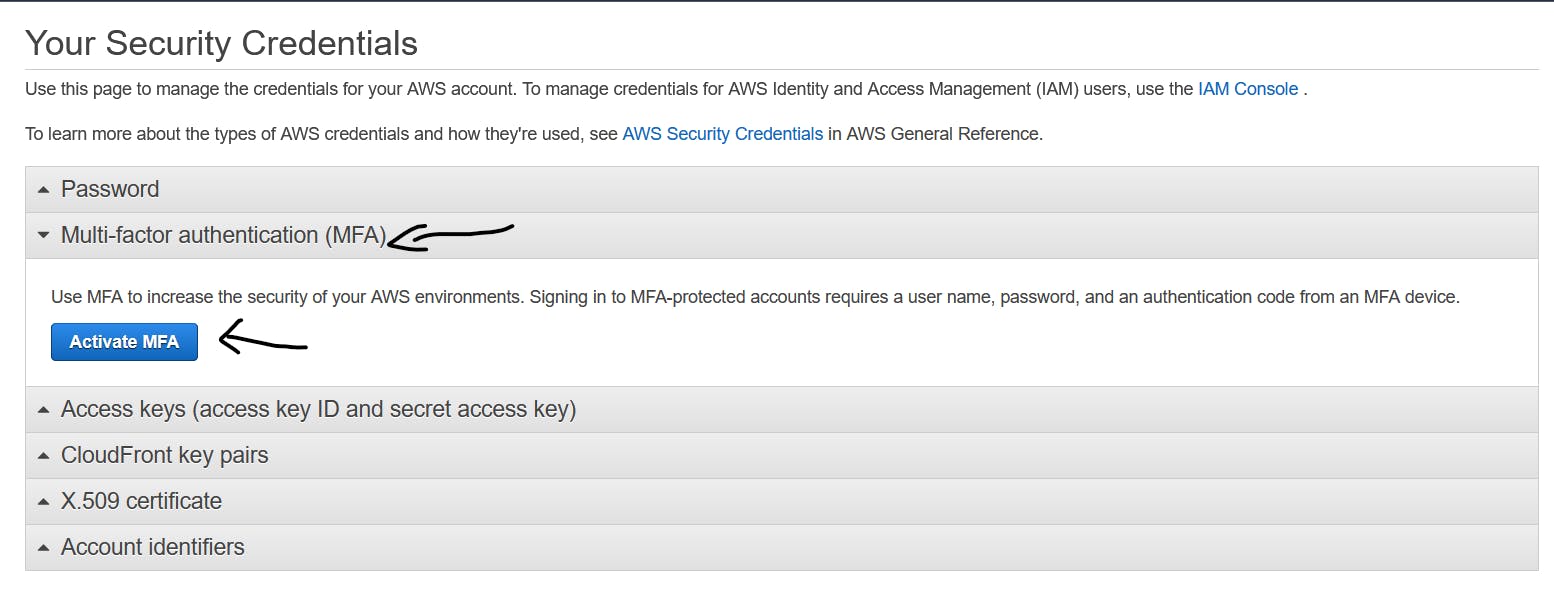
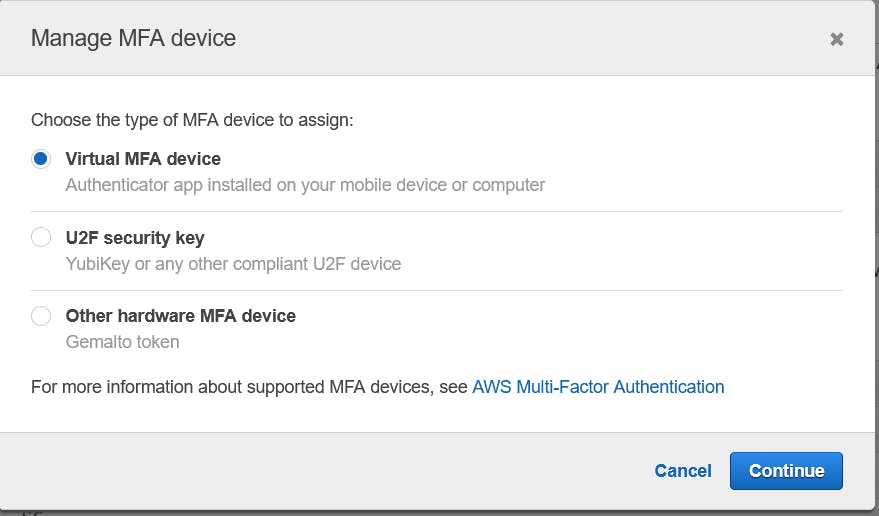
Now choose Virtual MFA for using MFA with Google Authentication app or any Authentication app.
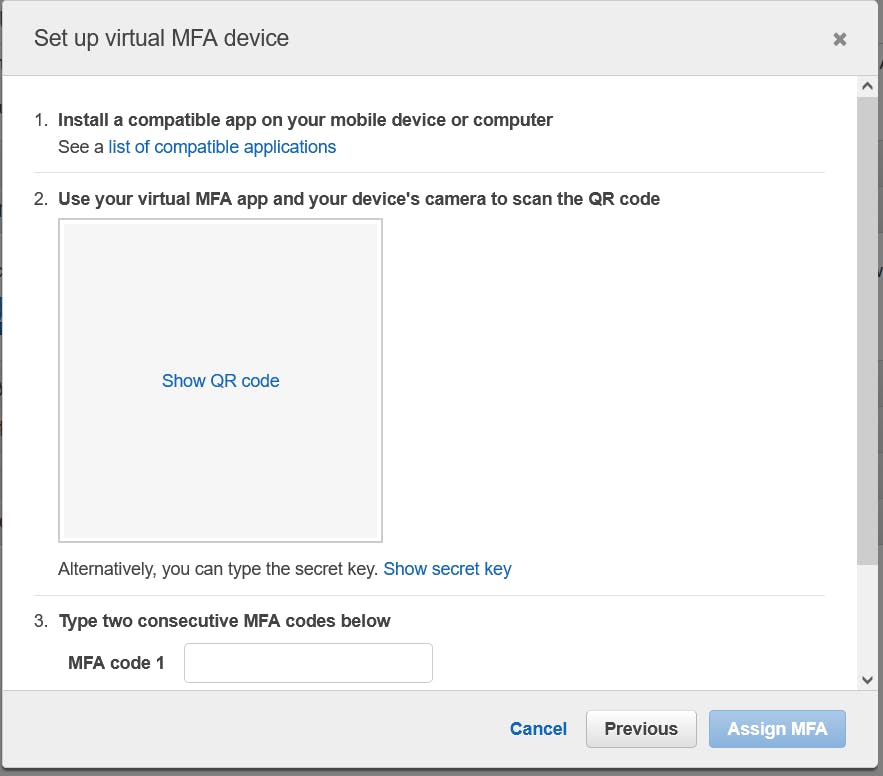
And then open your Google Authentication app and scan the QR code.
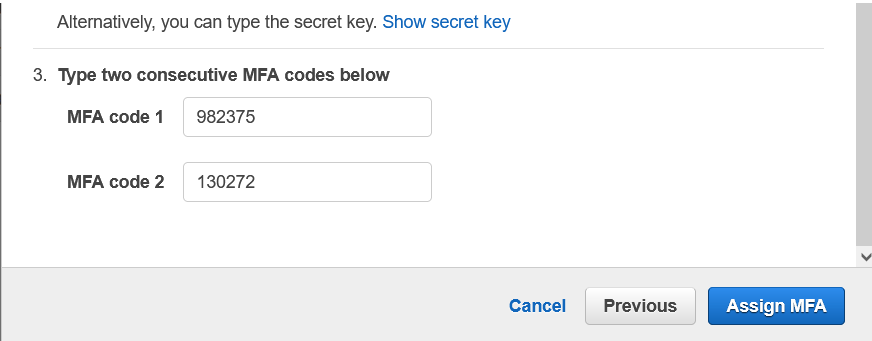
And Enter the Two Consiquite Code that displays on your APP. Note the code reshuffles every one Minute. so enter two codes sequentially And then Click on Assign MFA
Now Your Account is set with your MFA App (Google Authentication app). So now we shall go to cmd and access AWS CLI. If not installed please click here here to do so.
Remember that the AWS profile Should be the root AWS user, not an IAM User
aws s3api list-buckets
{
"Buckets": [
{
"Name": "mfatestbucket",
"CreationDate": "2021-09-05T06:25:20+00:00"
}
],
"Owner": {
"ID": "1ab1de8ca8eexxxxxxxxxxxxxxxxxxxxxxxxxxx"
}
}
Now we can see the created bucket in here. Now let's see how to enable the MFA.
aws s3api put-bucket-versioning
-- profile {root}
-- bucket {my-bucket-name}
-- versioning-configuration Status=Enabled,MFADelete=Enabled
-- mfa “{arn key} ”
This is the command structure. Remember '{' , '}' are not in the command they are just to let you see the variable parts.
aws s3api put-bucket-versioning -- is the command to put versioning in s3
Where { root } is the local root profile, Is your default profile is root you can ignore this.
bucket {my-bucket-name} is your bucket name
versioning-configuration Status=Enabled, MFADelete=Enabled - is to enable MFA
mfa {arn key } -- arn can be found in the MFA setting in the profile and Key = your Google authentication app key (( Remember they must be separated by space ))
Copy the arn key -- In the MFA setting as shown below. and hold on to it.
Let's see How this command works in my case.
aws s3api put-bucket-versioning
--profile root
--bucket mfatestbucket
--versioning-configuration Status=Enabled,MFADelete=Enabled
--mfa "arn:aws:iam::xxxxxxxxx:mfa/root-account-mfa-device 817166 "
This is the command I have Used with my case. Bacasue
- I have a profile named root which is the root of my AWS.
- I have bucket Name mfatestbucket
- I want versioning-configuration Status=Enabled, MFADelete=Enabled
- I have copied my ARN As shown above, and pasted it here from the Security Credentials page
- My Oauth token from google App Is 817166
In the same manner, you can also disable the MFA with the same command but With MFADelete = Disable
aws s3api put-bucket-versioning
--profile root
--bucket mfatestbucket
--versioning-configuration Status=Enabled,MFADelete=Disable
--mfa "arn:aws:iam::xxxxxxxxx:mfa/root-account-mfa-device 817166 "
And Finally The MFA has been activated
🙌🙌👋🙋♂️ Happy Learning 🙌🙌👋🙋♂️